Designs, Codes and Cryptography ( IF 1.4 ) Pub Date : 2024-10-18 , DOI: 10.1007/s10623-024-01486-8 Zahra Ahmadian, Akram Khalesi, Dounia M’foukh, Hossein Moghimi, María Naya-Plasencia
|
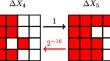
Truncated differential cryptanalyses were introduced by Knudsen in 1994. They are a well-known family of attacks that has arguably received less attention than some other variants of differential attacks. This paper gives some new insights into the theory of truncated differential attacks, specifically the conditions of provable security of SPN ciphers with MDS diffusion matrices against this type of attack. Furthermore, our study extends to various versions within the QARMA family of block ciphers, unveiling the only valid instances of single-tweak attacks on 10-round QARMAv1-64, 10-round QARMAv1-128, and 10- and 11-round QARMAv2-64. These attacks benefit from the optimal truncated differential distinguishers as well as some evolved key-recovery techniques.
中文翻译:

截断差分密码分析:QARMAv1-n 和 QARMAv2-64 的新见解和应用
截断差分密码分析由 Knudsen 于 1994 年推出。它们是众所周知的攻击系列,可以说比其他一些差分攻击变体受到的关注更少。本文对截断差分攻击的理论提供了一些新的见解,特别是使用 MDS 扩散矩阵的 SPN 密码针对此类攻击的可证明安全性的条件。此外,我们的研究扩展到 QARMA 分组密码系列中的各种版本,揭示了 10 轮 QARMAv1-64、10 轮 QARMAv1-128 以及 10 轮和 11 轮 QARMAv2-64 上唯一有效的单调攻击实例。这些攻击受益于最佳的截断差分区分器以及一些进化的密钥恢复技术。






























 京公网安备 11010802027423号
京公网安备 11010802027423号